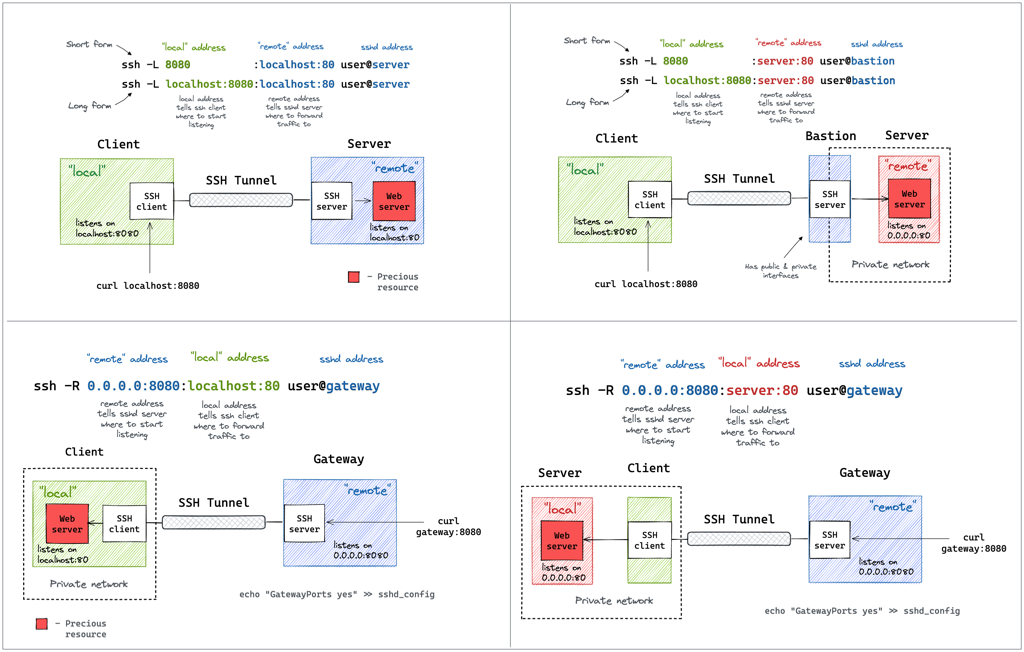
Introduce
OpenSSH is the premier connectivity tool for remote login with the SSH protocol. It encrypts all traffic to eliminate eavesdropping, connection hijacking, and other attacks. In addition, OpenSSH provides a large suite of secure tunneling capabilities, several authentication methods, and sophisticated configuration options.
GitHub Group: https://github.com/openssh
Source code: https://github.com/openssh/openssh-portable
Securing OpenSSH
SSHd config: /etc/ssh/sshd_config
Restart SSHd:
service sshd restart
Disable Root Logins
# Prevent root logins:
PermitRootLogin no
Limit User Logins
AllowUsers alice bob
Disable Protocol 1
# Protocol 2,1
Protocol 2
Disable Password Login
PasswordAuthentication no
Connection Multiplexing
OpenSSH 提供了许多强大的功能,其中之一就是 连接复用 (Connection Multiplexing),通过 ControlMaster、
ControlPersist 和
ControlPath 配置实现。
mkdir ~/.ssh/sockets/ chmod 700 ~/.ssh/sockets/
~/.ssh/config
Host *
ControlMaster auto
ControlPersist 10m
ControlPath ~/.ssh/sockets/%r@%k:%p
Extension
security key sk
h
ssh security key sk implementions:
- h
t t p s : / / g i t h u b . c o m / p g a s k i n / s s h - s k - p r o v i d e r - g m s - OpenSSH security key provider for Play Services on Android.
- h
t t p s : / / g i t h u b . c o m / m f r i e d l / s k - s g x - OpenSSH SK API implemented with Intel SGX
reference:
- h
t - U2F Key Support in OpenSSHt p s : / / d u o . c o m / l a b s / t e c h - n o t e s / u 2 f - k e y - s u p p o r t - i n - o p e n s s h
CA
View SSH cert:
$ ssh-keygen -L -f id_eddsa-cert.pub id_eddsa-cert.pub: Type: ssh-ed25519-cert-v01@openssh.com user certificate Public key: ED25519-CERT SHA256:m4BZYenmSmQCrogIeWXqAIRGgGlq511dvid2M1FqcaQ Signing CA: ECDSA SHA256:Dc6+i18g5P0sjnGhl+T1Lc+GQWPvn8QIqiOgjTg07rE (using ecdsa-sha2-nistp384) Key ID: "default_key_id" Serial: 2520885759318843550 Valid: from 2024-09-11T00:12:02 to 2024-09-11T01:12:03 Principals: root Critical Options: (none) Extensions: permit-port-forwarding permit-pty permit-user-rc permit-X11-forwarding permit-agent-forwarding
SSH CA
$ ssh-keygen -f server_ca Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in server_ca. Your public key has been saved in server_ca.pub. The key fingerprint is: SHA256:IRk7bvTPw7wkFXWVY8BoxxRpedhQ2rUqeBTX2B8V7AU hatterjiang@HatterJiangs-MacBook-Pro.local The key's randomart image is: +---[RSA 2048]----+ | . .**E=B| | + +o@o@+| | * . o.o.+o=| | o + .o. ...| | o S..o . | | . *. . | | . B | | o o | | . | +----[SHA256]-----+ $ ls -l total 16 -rw------- 1 hatterjiang staff 1675 Jul 8 03:12 server_ca -rw-r--r-- 1 hatterjiang staff 424 Jul 8 03:12 server_ca.pub
$ ssh-keygen -s server_ca -I host_auth_server -h -n test.example.com -V +52w user_key.pub Signed host key user_key-cert.pub: id "host_auth_server" serial 0 for test.example.com valid from 2016-07-08T03:14:00 to 2017-07-07T03:14:59 $ ls -l total 40 -rw------- 1 hatterjiang staff 1675 Jul 8 03:12 server_ca -rw-r--r-- 1 hatterjiang staff 424 Jul 8 03:12 server_ca.pub -rw------- 1 hatterjiang staff 1679 Jul 8 03:14 user_key -rw-r--r-- 1 hatterjiang staff 1377 Jul 8 03:14 user_key-cert.pub -rw-r--r-- 1 hatterjiang staff 424 Jul 8 03:14 user_key.pub
PIV CA
Step 1:
Generate SSH CA:
$ card-cli ssh-pub-key --ca -s r15 [INFO ] SSH algorithm: nistp384 cert-authority,principals="root" ecdsa-sha2-nistp384 AAAAE2VjZHNh****** Yubikey-PIV-R15
Step 2:
Write to file: ~/.ssh/authorized_keys.
Step 3:
Generate SSH key pair:
$ ssh-keygen -t ed25519 -f id_eddsa Generating public/private ed25519 key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in id_eddsa Your public key has been saved in id_eddsa.pub The key fingerprint is: SHA256:m4BZYenmSmQCrogIeWXqAIRGgGlq511dvid2M1FqcaQ hatterjiang@HatterJiang_macOS The key's randomart image is: +--[ED25519 256]--+ |B+ o. .. | |*o o... . ..o | |*o + .. . o E= | |=o+.o+o. . . + | |B+o++oo S o . | |= ...... o + = | | . . o . + o | | . | | | +----[SHA256]-----+
Step 4:
Generate SSH key pair cert:
$ card-cli ssh-piv-cert -f id_eddsa.pub -s r15 [INFO ] Serial: 2520885759318843550 [INFO ] Key ID: default_key_id [INFO ] Principals: ["root"] [INFO ] Validity: 3600 seconds
Step 5:
SSH to server:
$ ssh -i id_eddsa root@example.com Last login: Wed Sep 11 00:10:15 2024 from 115.*.*.* Welcome to Alibaba Cloud Elastic Compute Service ! [root@example ~]#
FIDO
From OpenSSH 8.2 which released on 2020-02-14 supports FIDO/U2F.
Linux releases uses OpenSSH 8.2:
- Ubuntu 20.04
resident-keys
ssh-keygen -t ecdsa-sk -O resident [-O verify-required]
Generate
ed25519keypair use
-t ed25519-sk
Generate ecdsa-sk sample:
$ ssh-keygen -t ecdsa-sk -O resident Generating public/private ecdsa-sk key pair. You may need to touch your authenticator to authorize key generation. Enter PIN for authenticator: Enter file in which to save the key (/Users/hatterjiang/.ssh/id_ecdsa_sk): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /Users/hatterjiang/.ssh/id_ecdsa_sk Your public key has been saved in /Users/hatterjiang/.ssh/id_ecdsa_sk.pub The key fingerprint is: SHA256:1YCKtRpHsN0saB2jlrPELq1gT+aRXD9BlI/Zo2c0y04 hatterjiang@HatterJiang_macOS The key's randomart image is: +-[ECDSA-SK 256]--+ | ..+o... | | . B+*. o | | @=++B . . | | .*=o=+.B | |...*++ oS + | |..=oo ..E | | .o = | | . | | | +----[SHA256]-----+
Restore resident public key:
$ ssh-keygen -K Enter PIN for authenticator: You may need to touch your authenticator to authorize key download. Enter passphrase (empty for no passphrase): Enter same passphrase again: Saved ECDSA-SK key to id_ecdsa_sk_rk
List credentials from Yubikey via ykman:
$ ykman fido credentials list Enter your PIN: Credential ID RP ID Username Display name 0156d3d2... ssh: openssh openssh
simple-ssh-server
For FIDO not supported server, use
simple-ssh-serverinstead.
Simple SSH server supports FIDO-U2F h
$ ssh -p 2222 root@hatter.ink Confirm user presence for key ECDSA-SK SHA256:+1wf4m+3FrZz5N9uvq4JkeCw69n2G3h6V7ymHC6GLlc User presence confirmed , . . . | . | | | | ) ) ,-. | ,-. ,-. ;-.-. ,-. |- ,-. |/|/ |-' | | | | | | | |-' | | | ' ' `-' ' `-' `-' ' ' ' `-' `-' `-' . . . . ,-. `. | | | | ' ( ` --- > |--| ,-: |- |- ,-. ;-. ,-. `-. ,-. ;-. . , ,-. ;-. ,' | | | | | | |-' | `-. . ) |-' | |/ |-' | ' ' `-` `-' `-' `-' ' `-' `-' `-' ' ' `-' ' [root@hatter simple-ssh-server]#
OpenPubkey
https://github.com/openpubkey/opkssh
opkssh is a tool which enables ssh to be used with OpenID Connect allowing SSH access to be managed via identities like alice@example.com instead of long-lived SSH keys. It does not replace SSH, but instead generates SSH public keys containing PK Tokens and configures sshd to verify them. These PK Tokens contain standard OpenID Connect ID Tokens. This protocol builds on the OpenPubkey which adds user public keys to OpenID Connect without breaking compatibility with existing OpenID Provider.
Currently opkssh is compatible with Google, Microsoft/Azure, Gitlab, hello.dev, and Authelia OpenID Providers (OP). See below for the entire list. If you have a gmail, microsoft or a gitlab account you can ssh with that account.
ssh
ForwardAgent
SSH agent forwarding allows you to use your private, local SSH key remotely without worrying about leaving confidential data on the server you're working with. It's built into ssh, and is easy to set up and use.
ssh -o "ForwardAgent yes" root@example.com
IMPORTANT: ForwardAgent only supports forward SSH_AUTH_SOCK
PKCS#11
OpenSC: h
ssh -I /Library/OpenSC/lib/opensc-pkcs11.so root@example.com
Yubikey PKCS#11:
- h
t t p s : / / d e v e l o p e r s . y u b i c o . c o m / y u b i c o - p i v - t o o l / Y K C S 1 1 / - h
t t p s : / / d e v e l o p e r s . y u b i c o . c o m / P I V / G u i d e s / S S H _ w i t h _ P I V _ a n d _ P K C S 1 1 . h t m l
ssh -I /usr/local/lib/libykcs11.dylib root@example.com
Yubikey PKCS#11 rust edition: h
ssh -I /FULLPATH/libyubikey_piv_pkcs11.dylib root@example.com
ssh-keygen
Generate new key
ssh-keygen -t rsa [-b 4096] -f id_rsa ssh-keygen -t ecdsa [-b 256] -f id_ecdsa ssh-keygen -t ed25519 -f id_eddsa
| Algorithm | Command |
|---|---|
ssh-rsa | ssh-keygen -t rsa |
ssh-ed25519 | ssh-keygen -t ed25519 |
ecdsa-sha2-nistp256 | ssh-keygen -t ecdsa -b 256 |
ecdsa-sha2-nistp384 | ssh-keygen -t ecdsa -b 384 |
ecdsa-sha2-nistp521 | ssh-keygen -t ecdsa -b 521 |
Show fingerprints
ssh-keygen -l -f id_rsa.pub [-E md5|sha1|sha256|sha384|sha512]
Public key to PKCS#8
ssh-keygen -e -f id_rsa.pub -m PKCS8
SSH signature
Sign with card-cli
$ echo hello | card-cli ssh-piv-sign -s 9a -n gitea --in - -----BEGIN SSH SIGNATURE----- U1NIU0lHAAAAAQAAAIgAAAATZWNkc2Etc2hhMi1uaXN0cDM4NAAAAAhuaXN0cDM4 NAAAAGEEQmzrrjuV14/UcNOH13QCP2Q5LYBP/SpSaBDrfeJV8Al6fbt/8hzPDtx8 FRaZJH5Od9pCEKSnk/A3Z0FvXWliD0tr2SWcl0m7MLiiKxyc5rW+oRadGgog3lIp 1Q8l7b1/AAAABWdpdGVhAAAAAAAAAAZzaGE1MTIAAACEAAAAE2VjZHNhLXNoYTIt bmlzdHAzODQAAABpAAAAMQCdJuat716djqAfp0Xz3sH8ZZbcCacotX+dSBL1TSDN jE4dRTcZu6946i4x8jpCgK0AAAAwCvbYW6IpO/LUe1qd5OA3xDN10BIQ+uIx3QGh Fwfz61ROqy2zLgrZLVprJ/NAt6uw -----END SSH SIGNATURE-----
Sign with ssh-keygen
$ echo hello | ssh-keygen -Y sign -n gitea -f id_ec Signing data on standard input -----BEGIN SSH SIGNATURE----- U1NIU0lHAAAAAQAAAGgAAAATZWNkc2Etc2hhMi1uaXN0cDI1NgAAAAhuaXN0cDI1NgAAAE EEMJ0CQ9x+h8EOazirYv5g8cQpmc99glbbwqobwQmdEGBSMQlA3eRI5aSA1qEIAlaKBueL VYuJT9/4lW+qWKBO2wAAAAVnaXRlYQAAAAAAAAAGc2hhNTEyAAAAYwAAABNlY2RzYS1zaG EyLW5pc3RwMjU2AAAASAAAACBYPhgCzNZWViFbt6DOX1xnWLZna5crs1s2cRb4qaji2gAA ACBFSNL3wukgQem5jnFUh3M0G2YZKoM4hf63OWvIJ1InfA== -----END SSH SIGNATURE-----
Verify
$ echo hello | ssh-keygen -Y check-novalidate -n gitea -s sig Good "gitea" signature with ECDSA key SHA256:ffQc4EuW8ZxSi0fhO3+anYiBD7PH92iNYxoyOCp3/lc
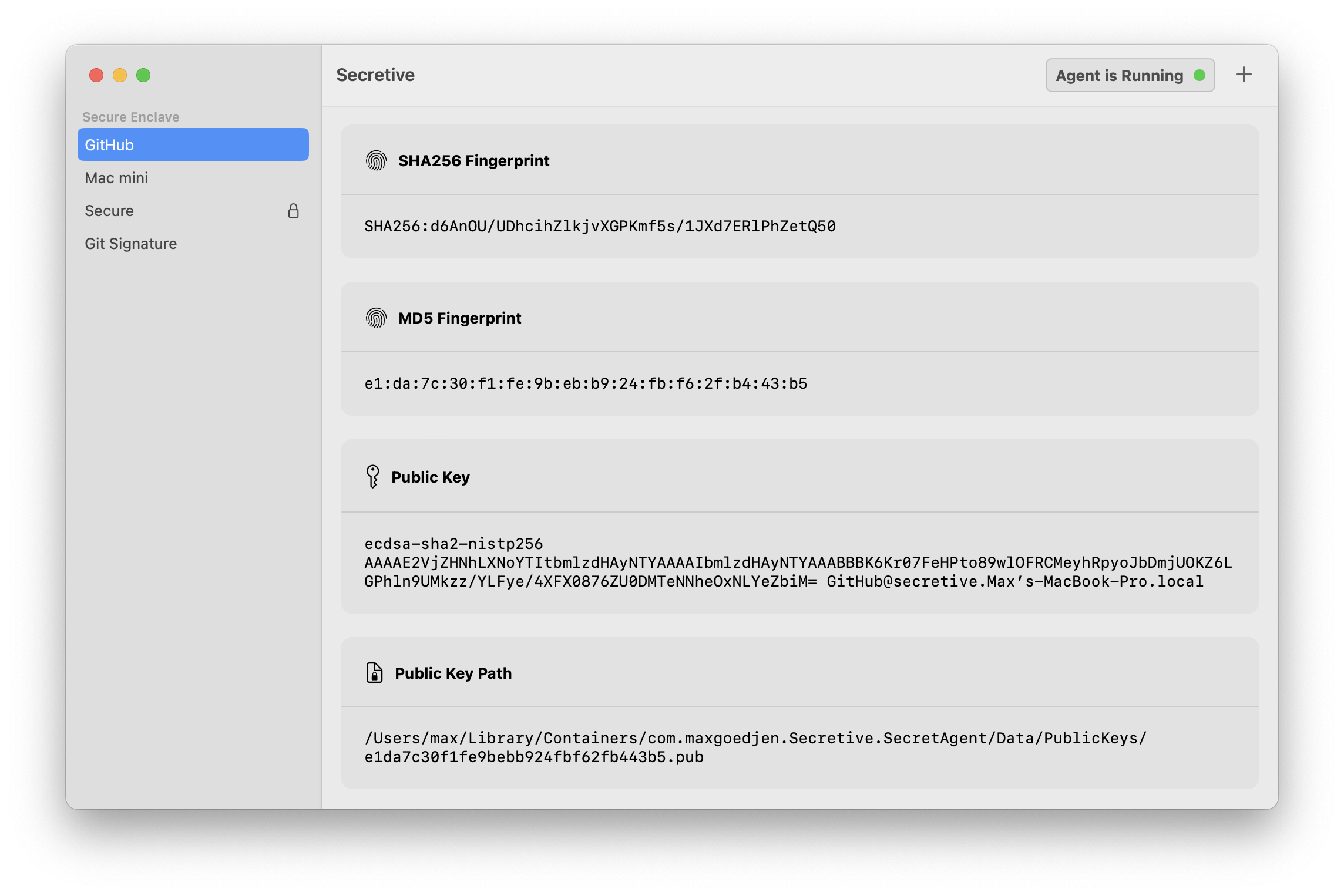
Secretive
h
Secretive is an app for storing and managing SSH keys in the Secure Enclave. It is inspired by the sekey project, but rewritten in Swift with no external dependencies and with a handy native management app.
Reference
- h
t t p s : / / g i t h u b . c o m / c l o u d t o o l s / s s h - c e r t - a u t h o r i t y - ssh-cert-authority
- h
t t p s : / / g i t h u b . c o m / c l o u d t o o l s / s s h - c a - ssh-ca
- h
t - How To Create an SSH CA to Validate Hosts and Clients with Ubuntut p s : / / w w w . d i g i t a l o c e a n . c o m / c o m m u n i t y / t u t o r i a l s / h o w - t o - c r e a t e - a n - s s h - c a - t o - v a l i d a t e - h o s t s - a n d - c l i e n t s - w i t h - u b u n t u - h
t - How to Harden SSH with Identities and Certificatest p s : / / e f . g y / h a r d e n i n g - s s h - h
t - Enhanced SSH and FIDO authentication in Ubuntu 20.04 LTSt p s : / / u b u n t u . c o m / b l o g / e n h a n c e d - s s h - a n d - f i d o - a u t h e n t i c a t i o n - i n - u b u n t u - 2 0 - 0 4 - l t s - h
t - Securing OpenSSHt p s : / / w i k i . c e n t o s . o r g / H o w T o s / N e t w o r k / S e c u r i n g S S H - h
t - A Visual Guide to SSH Tunnels: Local and Remote Port Forwardingt p s : / / i x i m i u z . c o m / e n / p o s t s / s s h - t u n n e l s / - h
t t p s : / / s u p e r u s e r . c o m / q u e s t i o n s / 3 0 8 1 2 6 / i s - i t - p o s s i b l e - t o - s i g n - a - f i l e - u s i n g - a n - s s h - k e y - h
t - Generating SSH keyst p s : / / c l o u d . i b m . c o m / d o c s / h p - v i r t u a l - s e r v e r s ? t o p i c = h p - v i r t u a l - s e r v e r s - g e n e r a t e _ s s h - h
t - GitHub now supports SSH security keyst p s : / / w w w . y u b i c o . c o m / b l o g / g i t h u b - n o w - s u p p o r t s - s s h - s e c u r i t y - k e y s / - h
t - Securing SSH Authentication with FIDO2t p s : / / d e v e l o p e r s . y u b i c o . c o m / S S H / S e c u r i n g _ S S H _ w i t h _ F I D O 2 . h t m l