Introduce
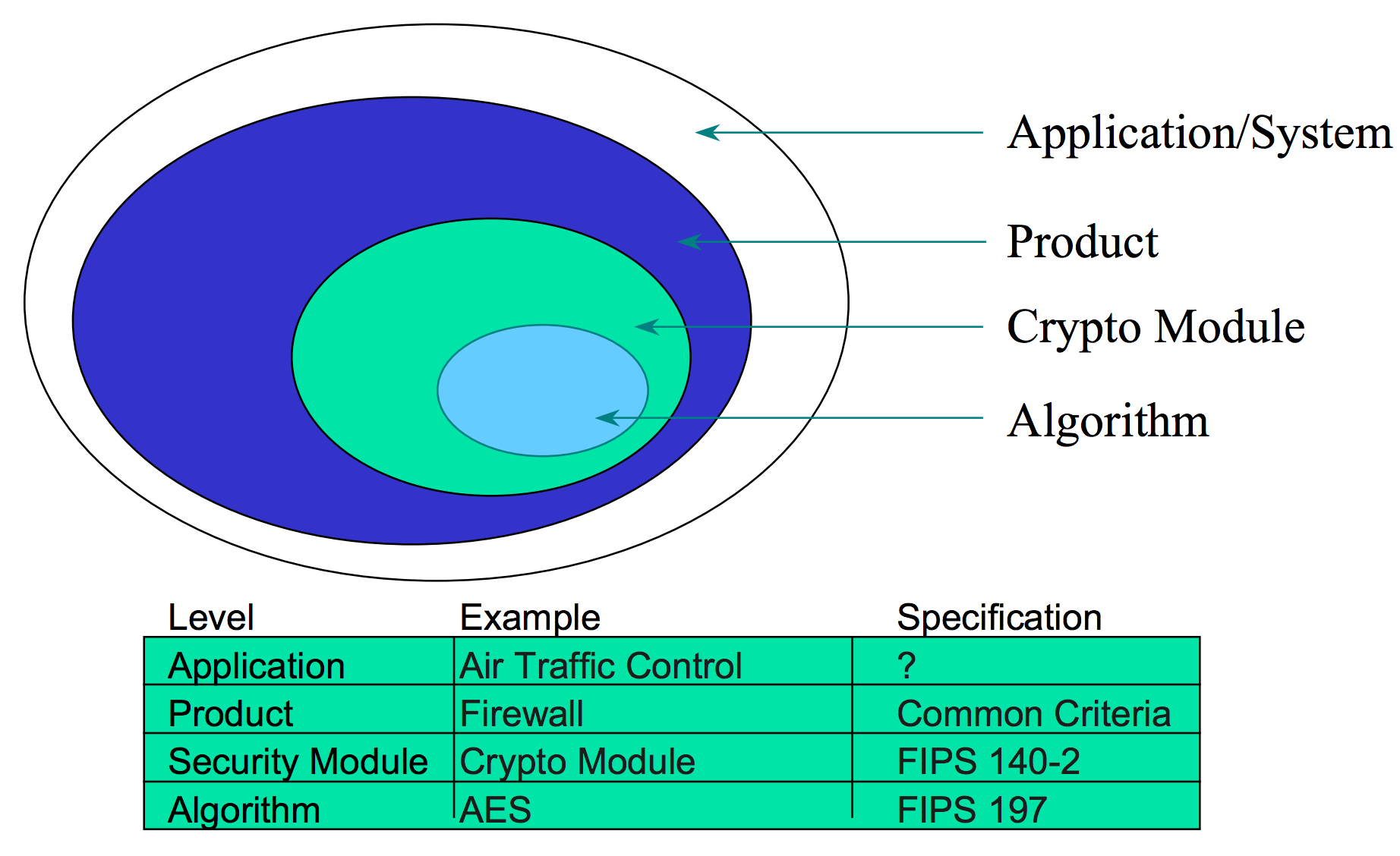
- FIPS 140-1
- Originally published in 1994
- Items tested under this standard are still valid
- FIPS 140-2
- Originally published in 2001
- FIPS 140-3
- Currently in draft form, publishing date unknown
- Drafting of the standard began in 2005
Software/Hardware/firmware that employs cryptographic services:
- Encryption
- Signature
- Hashing
- Authentication
- Key management (generation, storage, import, export)
Three key components to FIPS 140-2
- FIPS 140-2 Standard
- FIPS 140-2 Derived Test Requirements (DTR)
- FIPS 140-2 Implementation Guidance (IG)
Eleven Security Areas
- Cryptographic Module Specification
- Cryptographic Module Ports and Interfaces
- Roles, Services, and Authentication
- Finite State Model
- Physical Security
- Operational Environment
- Cryptographic Key Management
- EMI/EMC requirements
- Self Tests
- Design Assurance
- Mitigation of Other Attacks
Levels of Security
- Four levels - Level 1 thru Level 4
- Level 1 is the lowest, Level 4 most stringent
- Requirements are primarily cumulative by level
- Levels assigned for each of the 11 security sections
- Overall rating is lowest rating in all sections
- module must be configured and operated inaccordance with the level it was validated

CC Security Considerations For crypto Modules
- Level 1: No CC requirement
- Level 2: EAL-2 Evaluated OS
- Level 3: EAL-3 Evaluated OS
- Level 4: EAL-4 Evaluated OS
Approved Security Functions
- Symmetric Key – AES, Triple-DES, Skipjack
- Asymmetric Key –DSA, RSA, ECDSA
- Message Authentication – DES MAC, Triple-DES Mac, Enhanced Security DES, CCM Mode
- Hashing – Secure Hash Standard (SHS) – SHA-1, SHA-224, SHA-256, SHA-384 and SHA-512
- Keyed Hash – HMAC
- Random Number Generator –Approved Random Number Generators for FIPS 140-2, Security Requirements for Cryptographic Modules.
Related
- ISO/IEC 19790:2012 - Information technology – Security techniques – Security requirements for cryptographic modules
- FIPS 197 - Advanced Encryption Standard (AES)
- NIST SP 800-56A - Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography
- NIST SP 800-56B - Recommendation for Pair-Wise Key Establishment Schemes Using Integer Factorization Cryptography
- NIST SP 800-56C - Recommendation for Key Derivation through Extraction-then-Expansion
- NIST SP 800-131A - Transitions: Recommendation for Transitioning the Use of Cryptographic Algorithms and Key Lengths
- NIST SP 800-132 - Recommendation for Password-Based Key
Reference
- https://www.defcon.org/images/defcon-19/dc-19-presentations/Maresca/DEFCON-19-Maresca-FIPS-140.pdf
- https://www.ipa.go.jp/event/iccc2005/pdf/B2-04.pdf
- http://csrc.nist.gov/groups/STM/cmvp/documents/CMVP2002/proceed/CMVP2606.pdf
- http://csrc.nist.gov/groups/STM/cmvp/standards.html
- http://icmc-2013.org/wp/wp-content/uploads/2013/09/Weingart-Intro_to_FIPS_140-2.pdf
Cryptographic Module Validation Program (CMVP)
Derived Test Requirements (DTR)