Introduction
OpenPubkey
Official Git Group: https://github.com/openpubkey
The Linux Foundation, BastionZero and Docker are excited to announce the launch of OpenPubkey as a Linux Foundation open source project. To coincide with the launch of OpenPubkey, BastionZero is announcing the integration of OpenPubkey for Docker container signing, to help secure the open source software ecosystem with zero-trust passwordless authentication.
Signing Docker
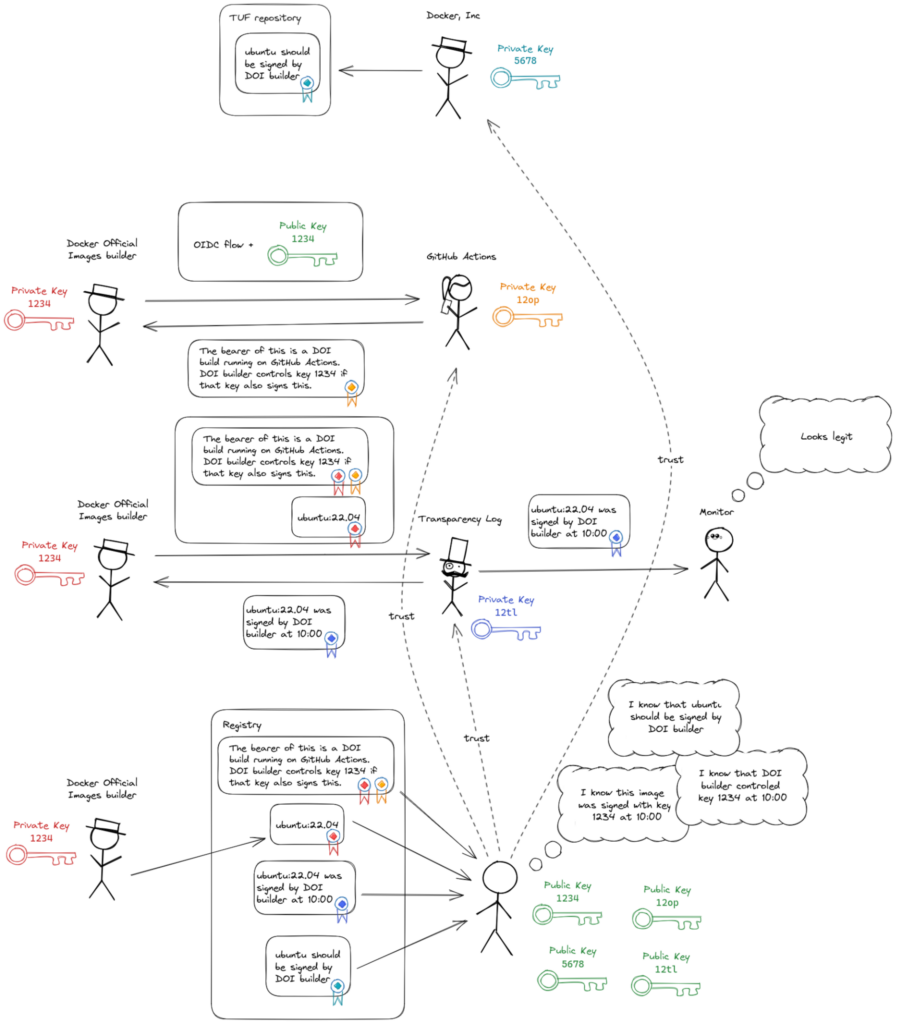
Before a CA issues a certificate, it needs to verify control of the private key and control of the identity. In Figure 10, the CA outsources the identity verification to an OIDC provider. We can already use the OIDC provider to verify the identity, but can we use it to verify control of the private key? It turns out that we can.
OpenPubkey is a protocol for binding OIDC identities to public keys. Full details of how it works can be found in the OpenPubkey paper, but below is a simplified explanation.
OIDC recommends a unique random number to be sent as part of the request to the OIDC provider. This number is called a nonce.
If the nonce is sent, the OIDC provider must return it in the signed JWT (JSON Web Token) called an ID token. We can use this to our advantage by constructing the nonce as a hash of the signer’s public key and some random noise (as the nonce still has to be random). The signer can then bundle the ID token from the OIDC provider with the public key and the random noise and sign the bundle with its private key.
The resulting token (called a PK token) proves control of the OIDC identity and control of the private key at a specific time, as long as a verifier trusts the OIDC provider. In other words, the PK token fulfills the same role as the certificate provided by the CA in all the signing flows up to this point, but does not require trust in a CA. This token can be distributed alongside signatures in the same way as a certificate.
OIDC ID tokens, however, are designed to be verified and discarded in a short timeframe. The public keys for verifying the tokens are available from an API endpoint hosted by the OIDC provider. These keys are rotated frequently (every few weeks or months), and there is currently no way to verify a token signed by a key that is no longer valid. Therefore, a log of historic keys will need to be used to verify PK tokens that were signed with OIDC provider keys that have been rotated out. This log is an additional point of trust for a verifier, so it may seem we’ve removed one point of trust (the CA) and replaced it with another (the log of public keys). For DOI, we have already added another point of trust with the TUF repository used to distribute trust policy. We can also use this TUF repository to distribute the log of public keys.
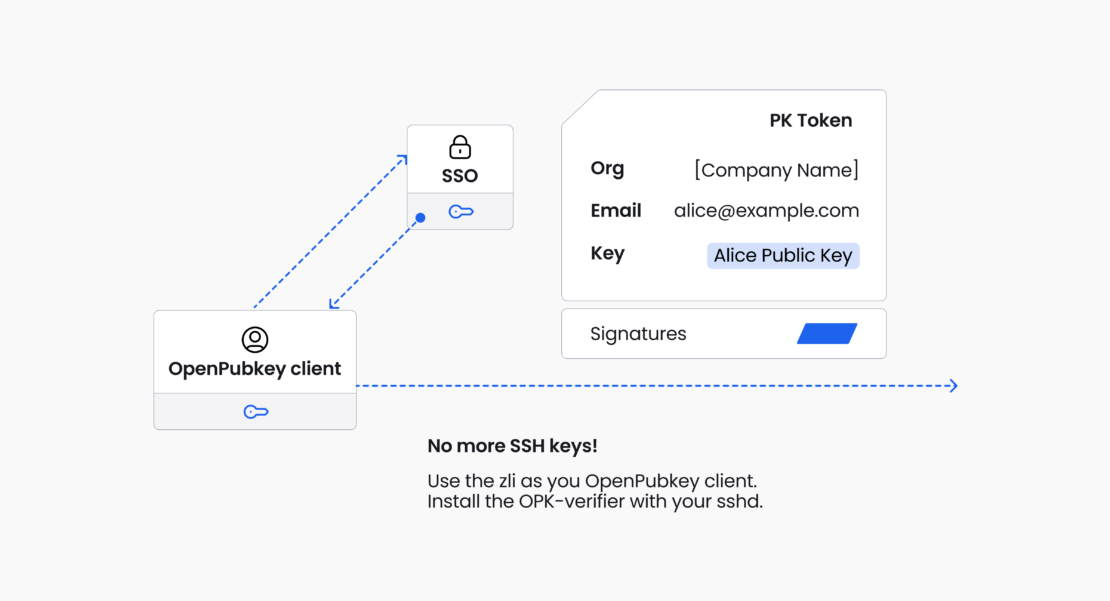
OpenPubkey SSH
https://github.com/openpubkey/opkssh
opkssh is a tool which enables ssh to be used with OpenID Connect allowing SSH access to be managed via identities like alice@example.com instead of long-lived SSH keys. It does not replace SSH, but instead generates SSH public keys containing PK Tokens and configures sshd to verify them. These PK Tokens contain standard OpenID Connect ID Tokens. This protocol builds on the OpenPubkey which adds user public keys to OpenID Connect without breaking compatibility with existing OpenID Provider.
Reference
- https://www.bastionzero.com/openpubkey
- https://eprint.iacr.org/2023/296.pdf
- https://github.com/openpubkey/openpubkey
- https://eprint.iacr.org/2023/296
- https://blog.sigstore.dev/openpubkey-and-sigstore/
- https://www.linuxfoundation.org/press/announcing-openpubkey-project
- https://github.com/openpubkey/openpubkey/blob/main/docs/FAQ.md
- https://www.docker.com/blog/how-to-use-openpubkey-to-solve-key-management-via-sso/ - How to Use OpenPubkey to Solve Key Management via SSO
- https://www.docker.com/blog/signing-docker-official-images-using-openpubkey/ - Signing Docker Official Images Using OpenPubkey